Seeking Efficiencies While Reducing Risk: Predictive Patching For Overburdened Enterprises
By Paulo Shakarian, CYR3CON
In mid-July, the media reported on Russian hackers stealing COVID-19 vaccine research. But perhaps the most interesting thing is that the hackers leveraged software vulnerabilities that were not only known since 2019 but were also known to be targets of attack. Why do these get overlooked?
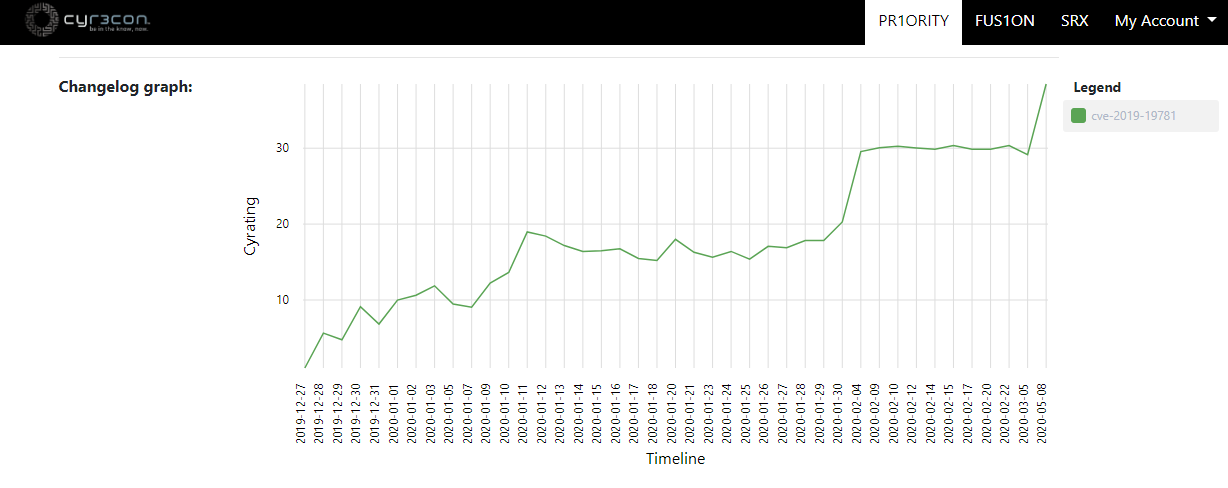
Machine learning-based predictions of one of the vulnerabilities used by Russian hackers to steal COVID-19 vaccine research that dates to 2019
The problem faced by the victims of Russian hackers is a growing one. With more than 10,000 new vulnerabilities disclosed in 2020 to date, it’s no wonder enterprises still fail to avoid breaches. In fact, 60 percent of chief information security officers (CISO’s) admit to being breached due to known, but unpatched, vulnerabilities.
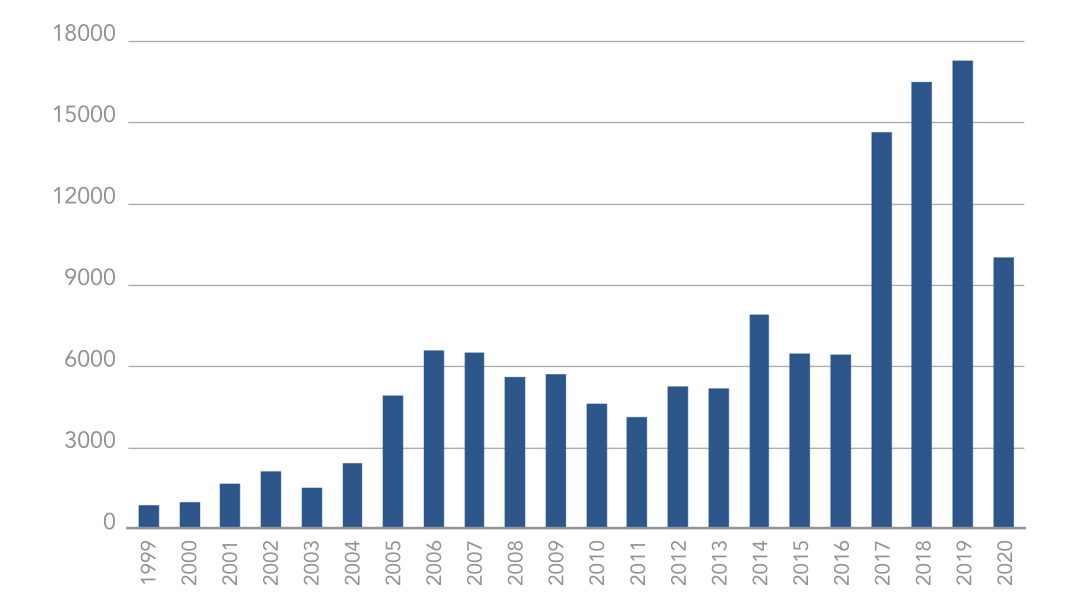
Vulnerability disclosures through mid-2020
Remote Work Increases Risk
The buildup of remote work capabilities due to the virus has exasperated this trend further. New technology is being rapidly deployed in cash-constrained environments. As a result, the ability of an attacker to strike has grown significantly. Other trends, such as increased usage of containers, virtualized operating systems that package up code to enable applications to run fast, also precipitate the problem.
Most of today’s VARs, MSPs, and MSSPs are effective in getting their customers up-and-running with vulnerability management software, conducting vulnerability scanning, and even penetration testing services. However, a common sentiment among most resellers and service providers is, “Our clients know where the vulnerabilities are but are too overwhelmed to do much about it.”
Some organizations have responded by throwing dollars and personnel at the problem. For instance, many of the larger financials invested outsized amounts to solve this problem –– utilizing a combination of intelligence and red teaming to “get inside” the hacker’s mind and base their predictions off that data. But this is not scalable. Nor is it very accurate. In fact, several scientific studies have revealed that hackers use only a small number of vulnerabilities (about 3 percent) in attacks – an interesting dichotomy that opens the door to a more innovative approach.
Thinking Like A Hacker
In 2015, the IARPA, a research funding agency under the Director of National Intelligence announced CAUSE, a program designed to forecast cyberattacks significantly earlier than existing methods. One of the key pieces of research to result from this program was machine learning algorithms to predict which vulnerabilities can be used by hackers.
The idea is to automatically gather hacker conversations from places like social media and the deep web then use that information to make predictions. With accurate predictions on which vulnerabilities will be exploited, security teams can make more informed decisions and mitigate the greatest risks first – hence avoiding breaches.
But the key is efficiency, focusing mitigation efforts based on what the adversary is using is simply more efficient and reduces risk at the same time. And this is exactly what is needed to reduce risk in organizations where budgets and resources are limited: the ability to predict what the adversary is going to do next and patch or mitigate accordingly. This is referred to as “predictive patching”. This way of viewing the problem keeps enterprises active in acting against threats while not requiring them to overtask their resources.
Building A Secure Environment For Enterprise Clients
Today, this technology is deployed in several large enterprises via a software-as-a-service (SaaS)-based platform. As a subscription-based service, it can complement an initial vulnerability scan or penetration test – allowing the enterprise to stay on top of evolving threats after the scan. It also makes it easier for VARs and MSPs to bundle with other tools like Qualys, Tenable, or Rapid7 – as it directly complements these capabilities.
This directly answers the enterprise question of “Where do we start?”. Once they get the result of the vulnerability scan, the prediction software allows them to rapidly reprioritize as new threats emerge. For clients with scanning already in-place, such prediction allows them to see when their mitigation efforts have fallen short, enabling them to resolve otherwise ignored threats.
Because the predictions are based on actual hacker discussions and distribution of exploits, the evidence behind the prediction is itself compelling. In fact, the identification of ignored threats to an enterprise along with the intelligence behind the threat is a way for a VAR, MSP, or MSSP to add value even during the sales process itself.
The move to the cloud also has increased the necessity for predictive intelligence. In that world, computing instances are deployed rapidly – often untracked by the security team. As organizations mature, they will move more toward a preventative posture – identifying vulnerabilities before an image is released. In this new fast-paced paradigm, the manual methods for dealing with the problem of prioritizing vulnerabilities fall woefully short as it cannot support real-time container activities –– and this presents a real opportunity for VARs, MSPs, and MSSPs to become cybersecurity coaches to their clients to ensure their assets are protected over the long term.
About The Author
Paulo Shakarian, Ph.D. is the cofounder and CEO of CYR3CON, a predictive cybersecurity technology originally funded under the CAUSE program and has recently raised over $8M to commercialize this technology to bring prediction to the enterprise. Today, multiple Fortune 500 companies use CYR3CON to stay ahead of threats.
